On Feb. 9, 2016, a test phishing message was sent to a number of University of Delaware employees. About 18% of the recipients were hooked by the phish. (UDaily story)
The test was designed to mimic spear phishing attacks that the University has recently observed. Spear phishing, a highly dangerous and increasingly common form of phishing, uses the names, logos, events and information of a legitimate company or group to trick victims into believing that the phishing emails are legitimate communications. Spear phishers might, for example, use the logos and names of executives of a major bank or university to send targeted emails designed to fool employees of that bank or university.
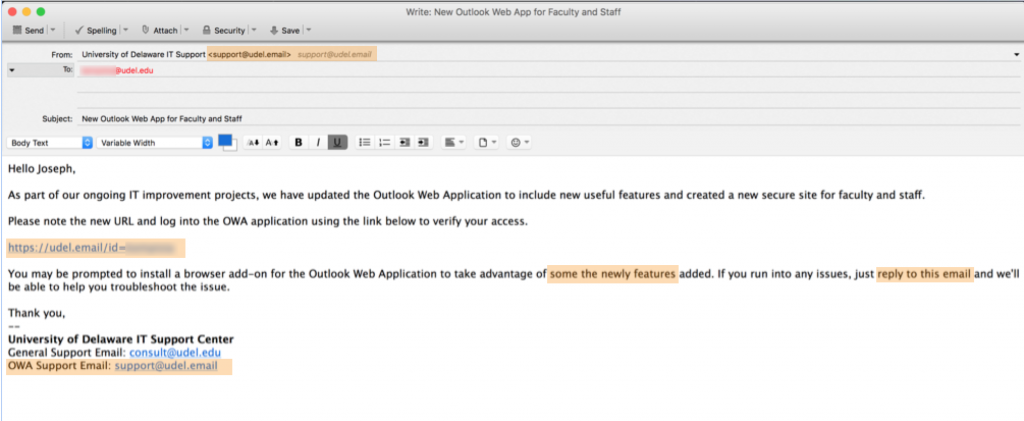
Below is a sample of the message sent:
The message uses a mixture of true information and untrue (but believable) information.
- It uses the recipient’s true first name and true UDelNet ID.
- The first sentence talks about ongoing improvements, new features, a secure site for faculty and staff, and “Outlook Web Application.” Yes, some UD employees use OWA, but not all employees do.
- The message also uses specific tricky yet detectable tactics to fool University of Delaware employees (highlighted with orange shading):
- The message comes from support@udel.email. UD email addresses all end with udel.edu.
- The link they want you to click also is a udel.email link. Nice touch using the recipient’s UDelNet ID as part of the link, but the recipient should, again, see that the URL is not a udel.edu address.
- The last paragraph contains a strange typo/grammatical mistake that should ring an alarm bell: “some the newly features.”
- The message asks you to reply to the message. The sender sounds so helpful. However, when you receive a suspicious message, the proper way of verifying it is not replying to it, but using published directory information to call, read about, or email the alleged sender.
- The signature is nearly convincing. It gets the name of our help desk correct (IT Support Center), and includes the real email address for the ITSC (consult@udel.edu). But look at the OWA Support email address. Does it end in udel.edu?
Those who clicked the link were taken to a website that is looks just like UD’s OWA login page. The only difference was the URL. The correct URL for UD’s OWA page is https://owa.win.udel.edu — a legitimate udel.edu URL. The bogus page used the URL https://udel.email.
If someone supplied their UDelNet ID and password to log in, they were taken to a Web page that included a stolen UD Logo:
Again, the URL points to udel.email. A bogus site!
Further, the page includes a “Click HERE” link for the download. Never download any software from a NON-trusted source.
If this had been a legitimate University of Delaware update, you would have been directed to download something from the UDeploy server or to go to a legitimate Microsoft update site.
This phishing test was specially designed for the University. However, it used tactics we have seen used by spear phishing scams.
If you receive email of which you are suspicious, take these precautionary steps:
- Report it to your department’s IT staff or to the IT Support Center.
- Look up the published contact information for the alleged sender and contact them about the suspicious message.
- Study the links in a message before your click any of them.
- Do not download unexpected email attachments.
To the vast majority of the UD employees who deleted this message, we say, “Good job.” To the rest of you we say, Think B4 U Click!