Campus has been busy these past few days. Students and professors alike are returning to the area, and there’s lots of communication going on between colleagues and UD’s many departments.
Unfortunately, this time also presents a golden opportunity for phishers looking to take advantage of the turmoil. We received several rapid-fire reports of phishing scams sent to UDel inboxes from various cyber criminals. We’ve posted four of them below.
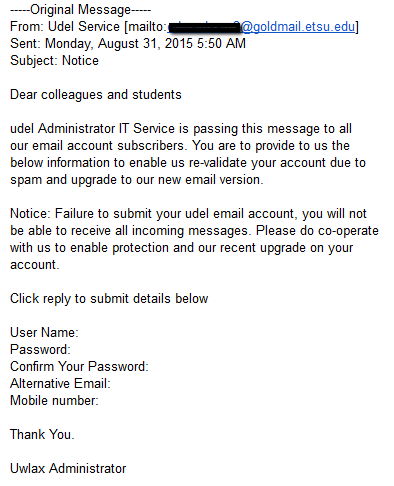
These emails are all obvious scams. Remember to look for the following characteristics of phishing emails:
- A sense of urgency—Phishers try to rush you into a hasty decision by setting deadlines and consequences for inaction. For example, a typical phish might claim that your email account will be deactivated or your network access terminated.
- A demand for information—Phishers will demand that you provide information or take action. Often, you’re asked to provide your email address and password. Legitimate business emails will never ask you for this information.
- A suspicious or fake link—Always check the links before you click on anything in an email. Hover your mouse cursor over a hyperlink to reveal the actual destination; never trust the link’s text. Phishers use bogus links to take unsuspecting victims to malicious pages that either infect your computer with malware or trick you into providing information. Often, they will create a fake site that looks very much like a real Web page from the business they’re impersonating, and you’ll be asked to “log in” through this page. If you do, the hackers will grab your account info!
- A suspicious sender—Make sure that the sender’s email address matches the individual or group that claimed to send you the email. Hackers will often use compromised or fake accounts to send phishing emails. If you get an email from another institution claiming to be from UD, it’s an obvious scam.
- Poor grammar, weird word choice, and other mistakes—Often, phishing emails contain grammatical errors, strange formatting, or weird word choice. For example, one of the emails below claims to come from “UD Web Portal” rather than a real UD department.
If you have doubts about the legitimacy of an email, contact the IT Support Center or the alleged sender (send a separate email to that person or group) and ask how to verify the content.
Never click suspicious links in email, never provide personal information in reply to an email, and never open unexpected attachments.