UD has partnered with the US Department of Homeland Security (DHS) to conduct security tests on UD’s systems and employees. As part of this effort, the DHS launched a simulated phishing attack on UD email accounts starting on June 3.
Three emails were designed using spear phishing tactics: they included references to UD programs, systems, and departments as well as fake senders and links in an attempt to trick users into clicking. In a real phishing attack, these links would have been malicious and could have infected users’ devices with malware or tricked users into surrendering account access or sensitive information. As test emails, though, they redirected users to a UD Web page highlighting the dangers of phishing attacks and the need to identify and avoid them.
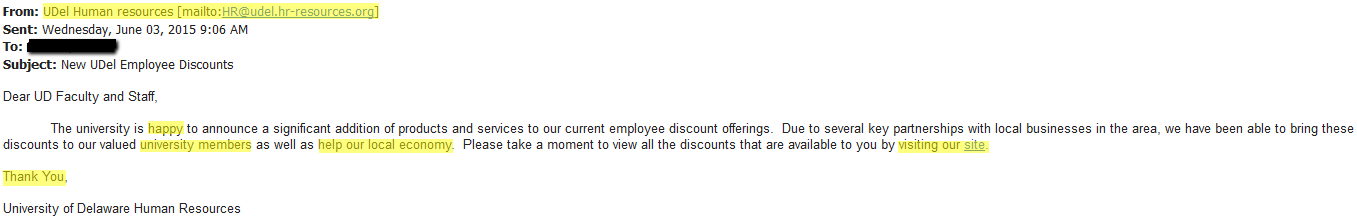
The first email advertises employee discounts at local stores. A quick read reveals awkward wording, such as “university members” instead of “University community.” The capitalization of the “Thank You” is also incorrect. The sender’s ID is a fake department (UDel Human resources vs. UD Human Resources), and the address is fake as well (note the .org domain). Finally, hovering over the clickable link reveals that “our site” is not actually a udel.edu address; it goes to “udel.hr-resources.org” instead!
The second email warns users of an upcoming network access reset and urges them to validate their credentials to avoid access termination. This message uses classic phishing tactics: it creates a false sense of urgency with the reset deadline, includes unfamiliar or fake technical jargon to fool average users, and demands that users provide account credentials in order to avoid something. It even references CAS and UDelNet ID (which are real UD terms) to create a more convincing illusion. The sender’s ID and the signature do not match; the sender claims to be “UDel Information Technology” (a fake department), but signs the email “University of Delaware Information Technologies.” As before, the sender’s address and the clickable link are from a fake domain: “udelit.no-reply-info.com.”
The third email advertised upgrades to users’ Google Apps for Education accounts and required that they validate their credentials to get access. Note the poor grammar, incorrect capitalization and punctuation, and weird wording throughout the email. The message urges users to act soon by stating that earlier requests will be given priority. This time, the sender’s ID and signature match each other more closely, but they still use a fake department and address. The clickable link once again goes to “udelit.no-reply-info.com,” a fake and suspicious domain.
If you’re one of the 7,300 users who received one of the above phishing emails, you should have spotted at least some of these signs that the message was a scam. If you didn’t, or if you missed a few of them, you should review these resources on identifying phishing emails: